Token Ring in Computer Networks
Overview
The token is a 3-byte small-size frame. And the token ring is one of the communication protocols in the Local Area Network(LAN). In a token ring, devices are connected in a ring topology and exchange tokens with each other. A token is required for a station to transmit data.
What is Token Ring in Computer Networks?
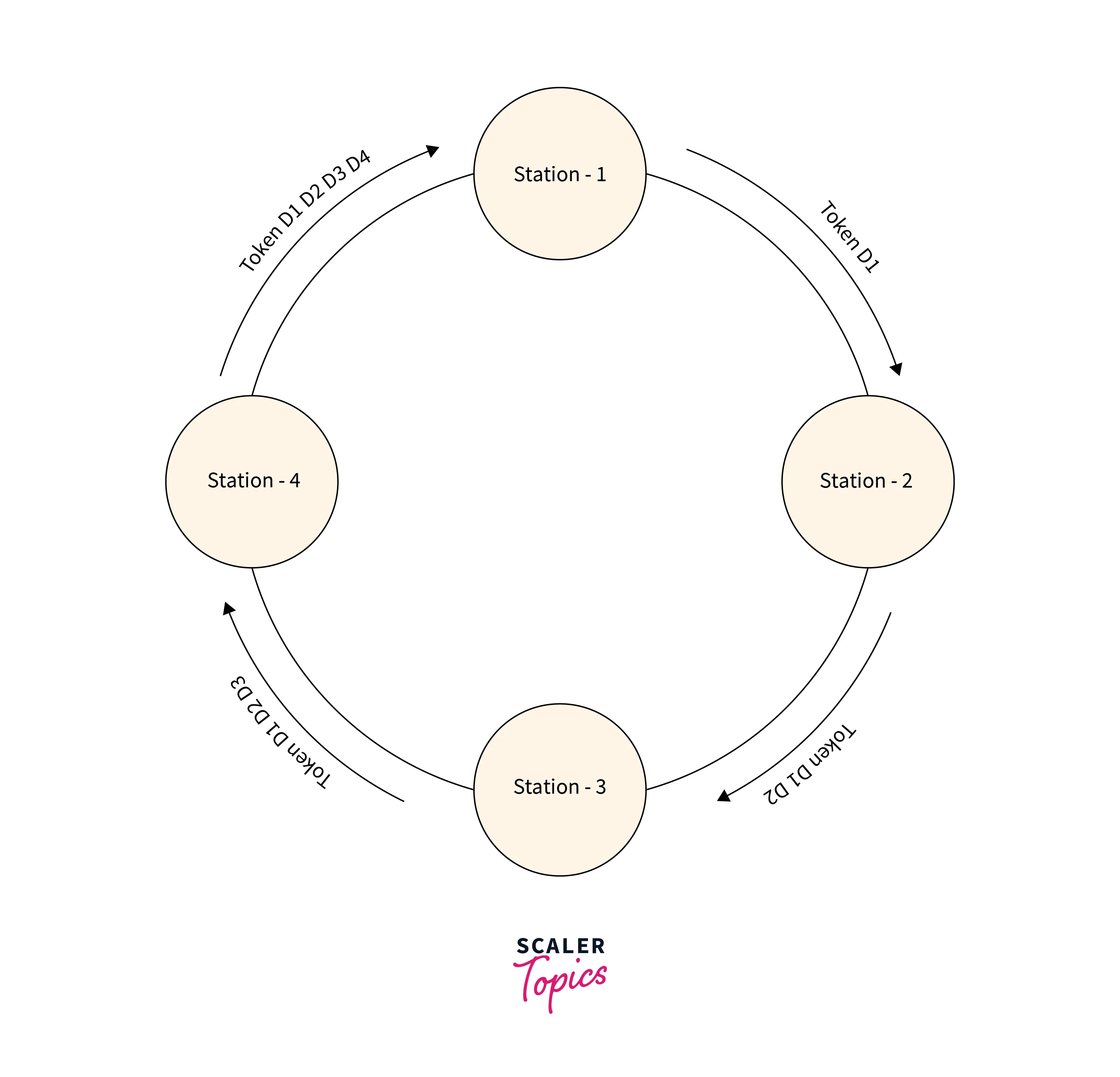
A token ring is defined as a communication protocol in a local area network in which all the stations present in the network are connected through a ring topology. The token is a small size frame of 3 bytes. It circulates among the stations in a ring. The station can only send frames if it has a token. After the successful transmission of the frame, it releases the token for further transmission by other stations.
A ring topology is an architecture of the network in which devices are connected in the form of a ring structure and transmit data to their neighboring node. Refer to the below image for the token ring
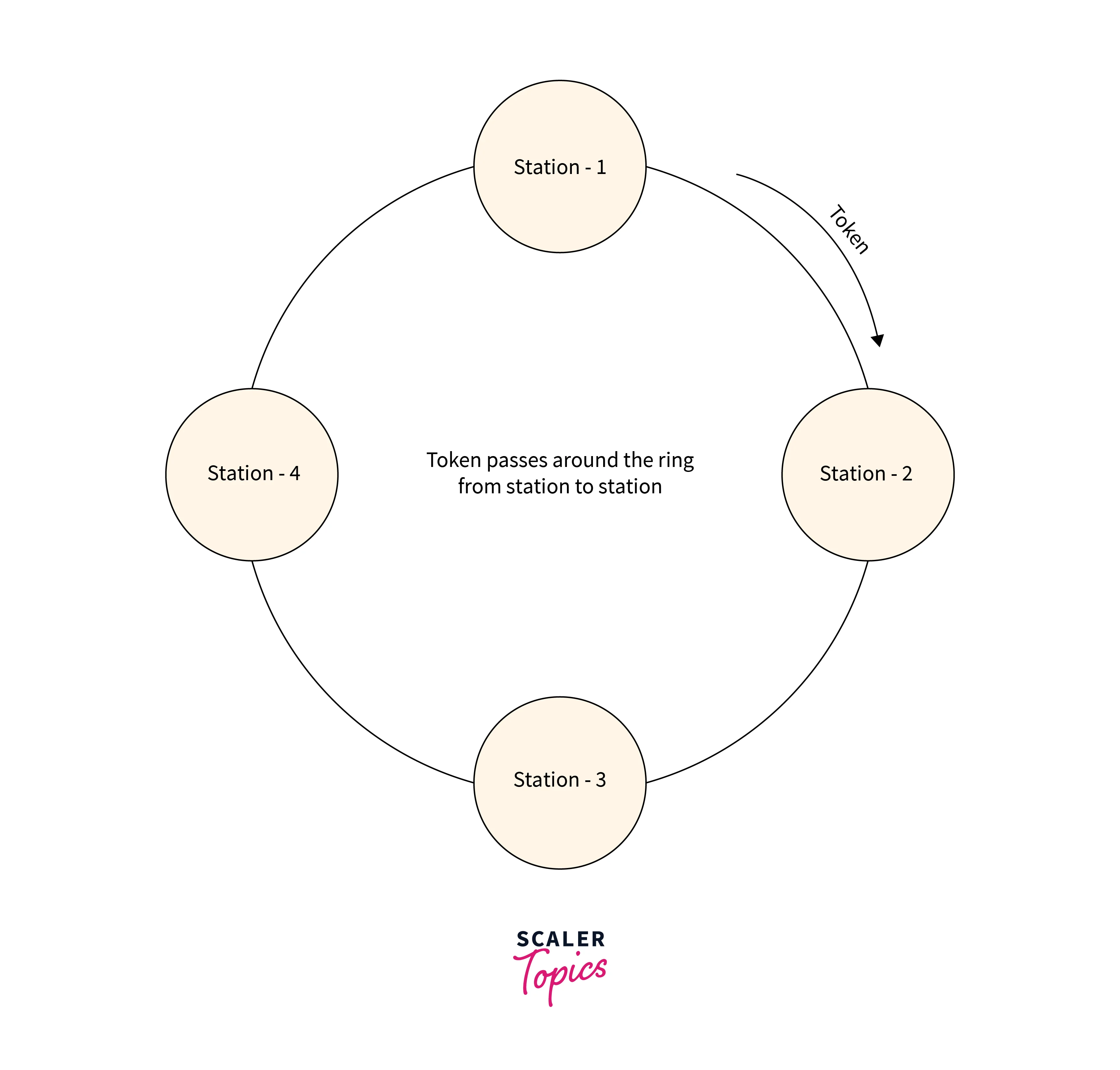
All the stations in the token ring network are connected physically.
How Does A Token Ring Work?
A Frame or packet reaches the next station according to the sequence of the ring.
- The frame or packet reaches the next station according to the sequence of the ring.
- Whether the frame contains a message addressed to them is determined by the current node. If yes, then the message is removed by the node from the frame. If not, then there is an empty frame(an empty frame is called the token frame).
- A Station that has the token frame, only has the access to transfer the data. If it has data then insert that data into the token frame otherwise release that token for the next station. The next station picks up that token frame for further transmission.
For the avoidance of network congestion, token rings allow only one device to be active at a time. The above steps are repeated by all the stations present in the token ring network. The size of the token is 3 bytes and it has a start and end delimiter that defines the beginning and the ending of the frame. It also has an access control byte within it. 4,500 bytes can be the maximum possible size of the data portion.
Modes of Operation
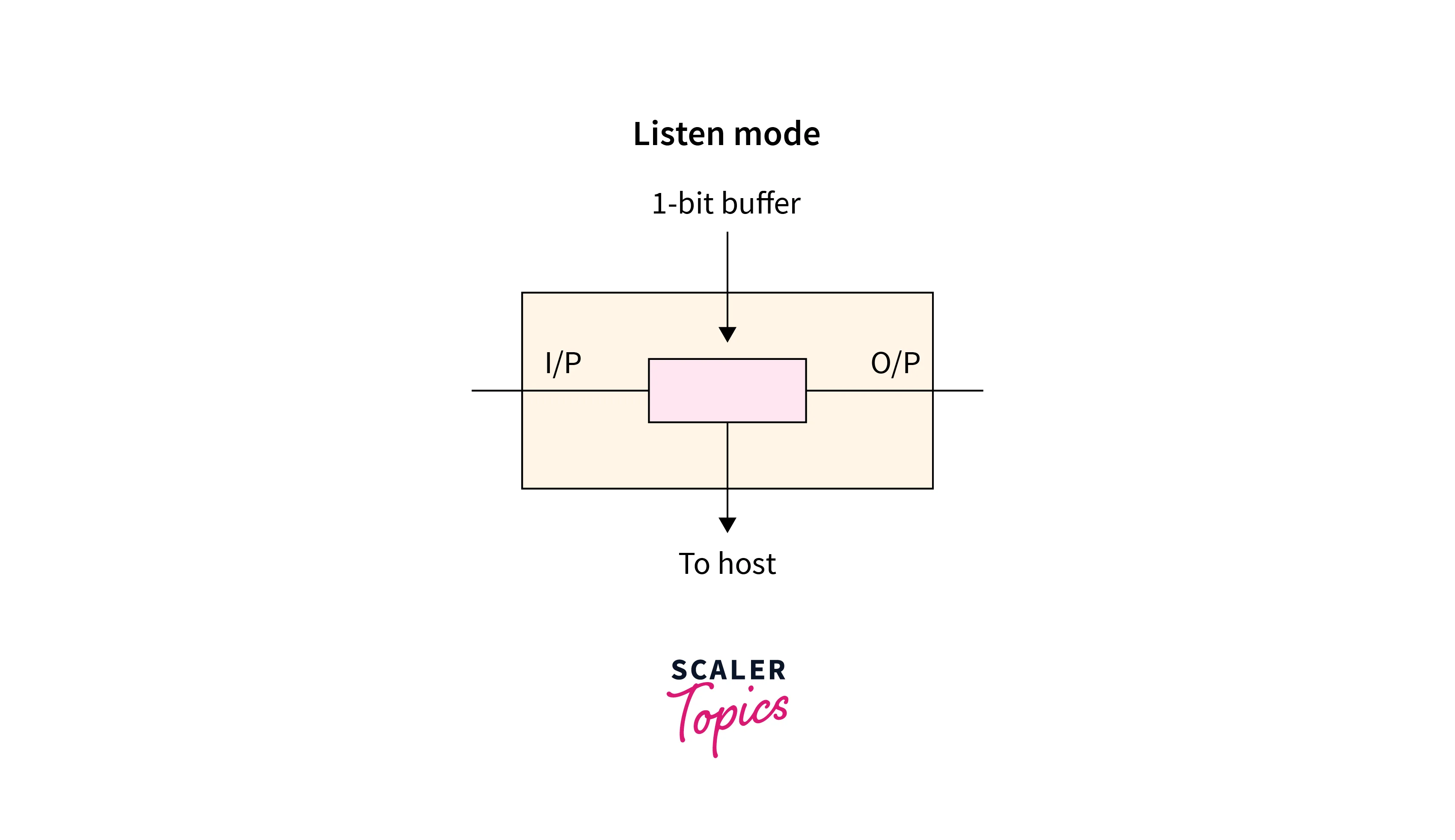
Listen Mode
In listen mode, the data is sent to the next node only when the node listens to the data. There is only a one-bit delay related to the transfer process.
Refer to the below image for the listen mode
Transmit Mode
Any data can be discarded by the node in transmit mode. And puts the data onto the network.
Refer to the below image for the transmit mode
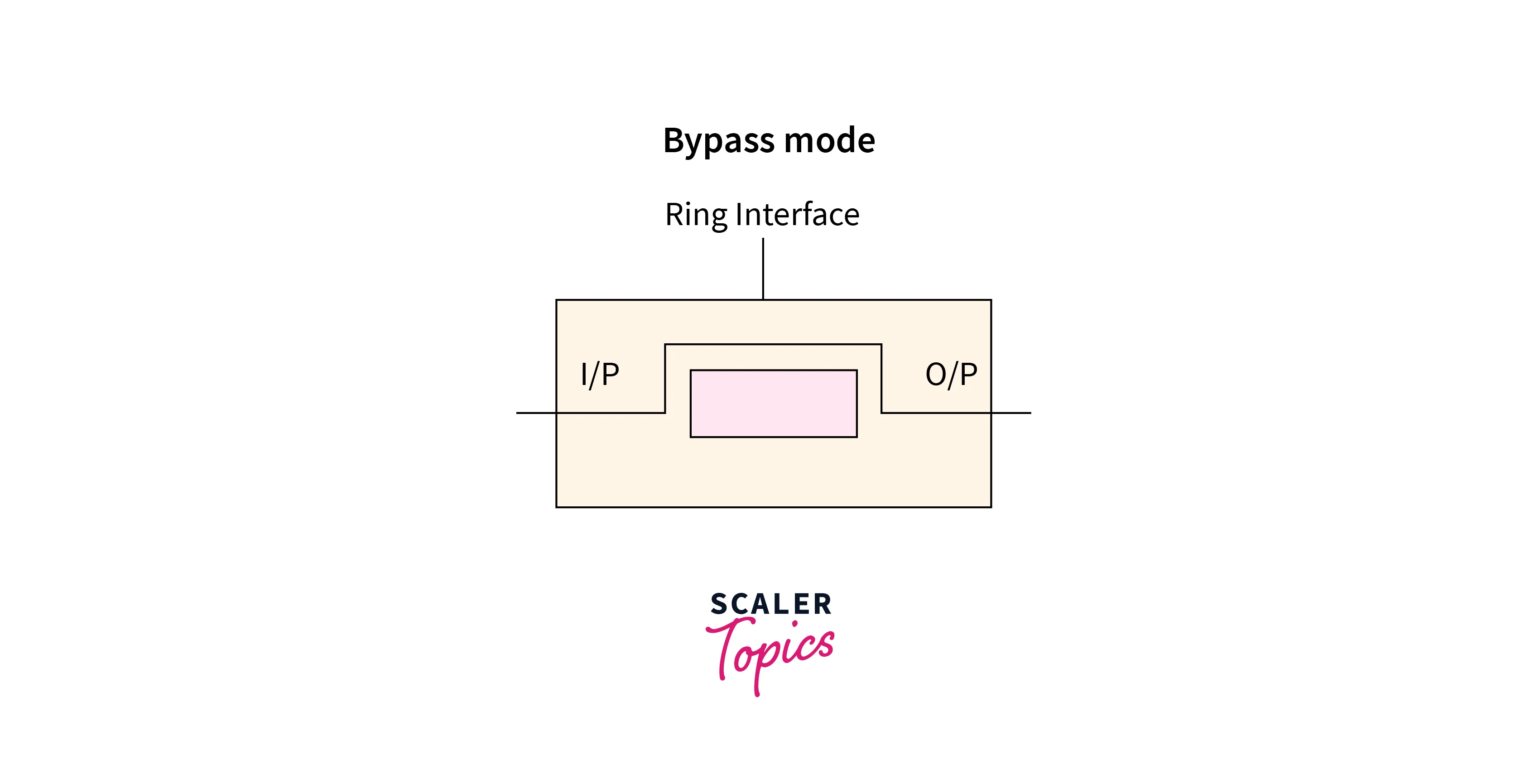
By-pass Mode
Whenever the node is down, bypass mode takes place. Using this mode, any data can be by-pass. No one-bit delay occurs in this mode.
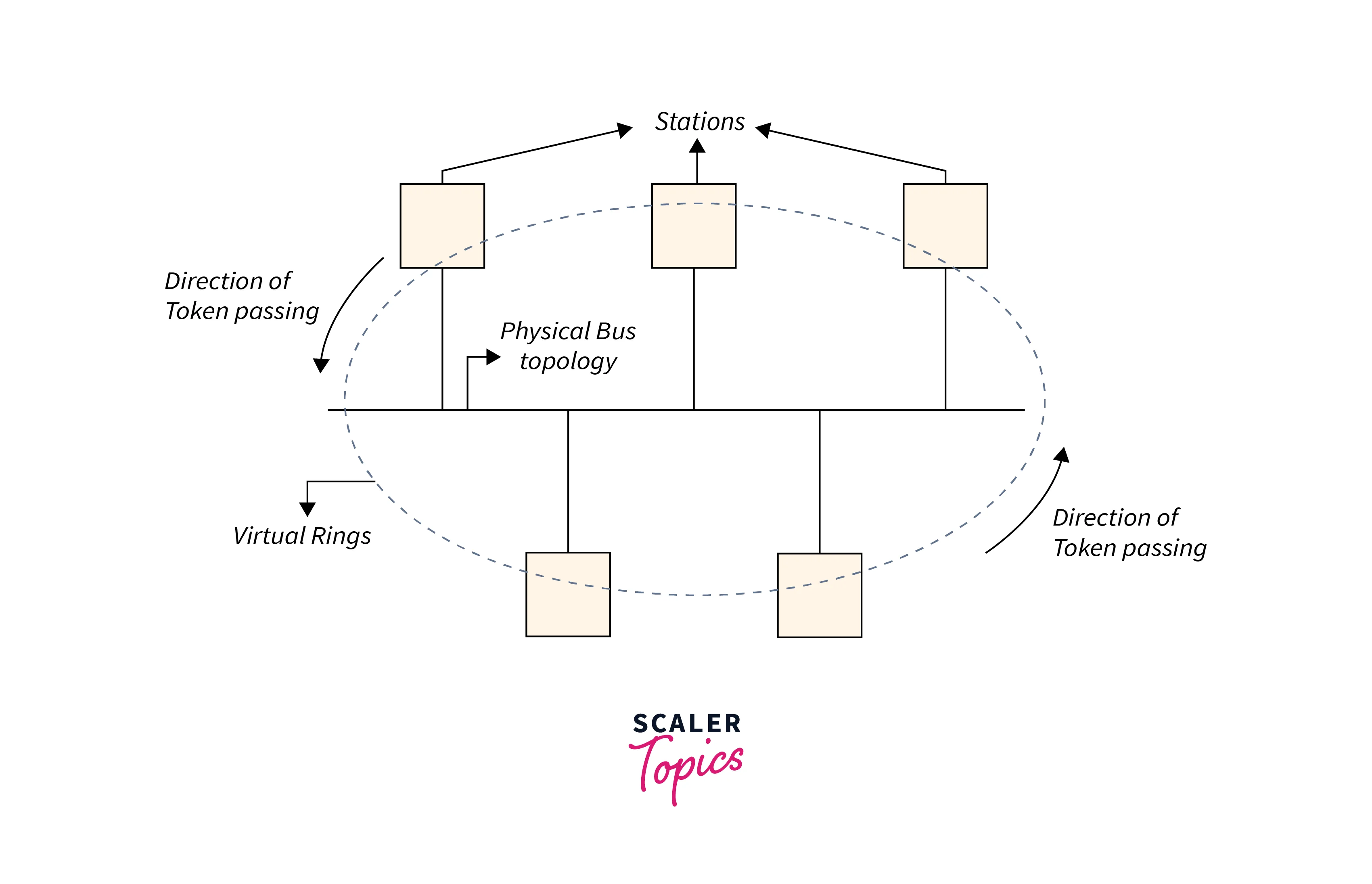
Token Passing Mechanism in Token Ring
A token is generally a short message. Its main work is to circulate in the network pass through the stations in the network and allow them to transfer the packet. The station that received the token can transfer the information and it can pass the token to another station if it does not have anything to transfer. This can also be explained through the following diagram Refer to the below image for the token-passing mechanism
Efficiency of Token Ring
Ring Latency
Ring latency is the time required for traveling the single bit around the ring.
Refer to the below image for the ring latency formula
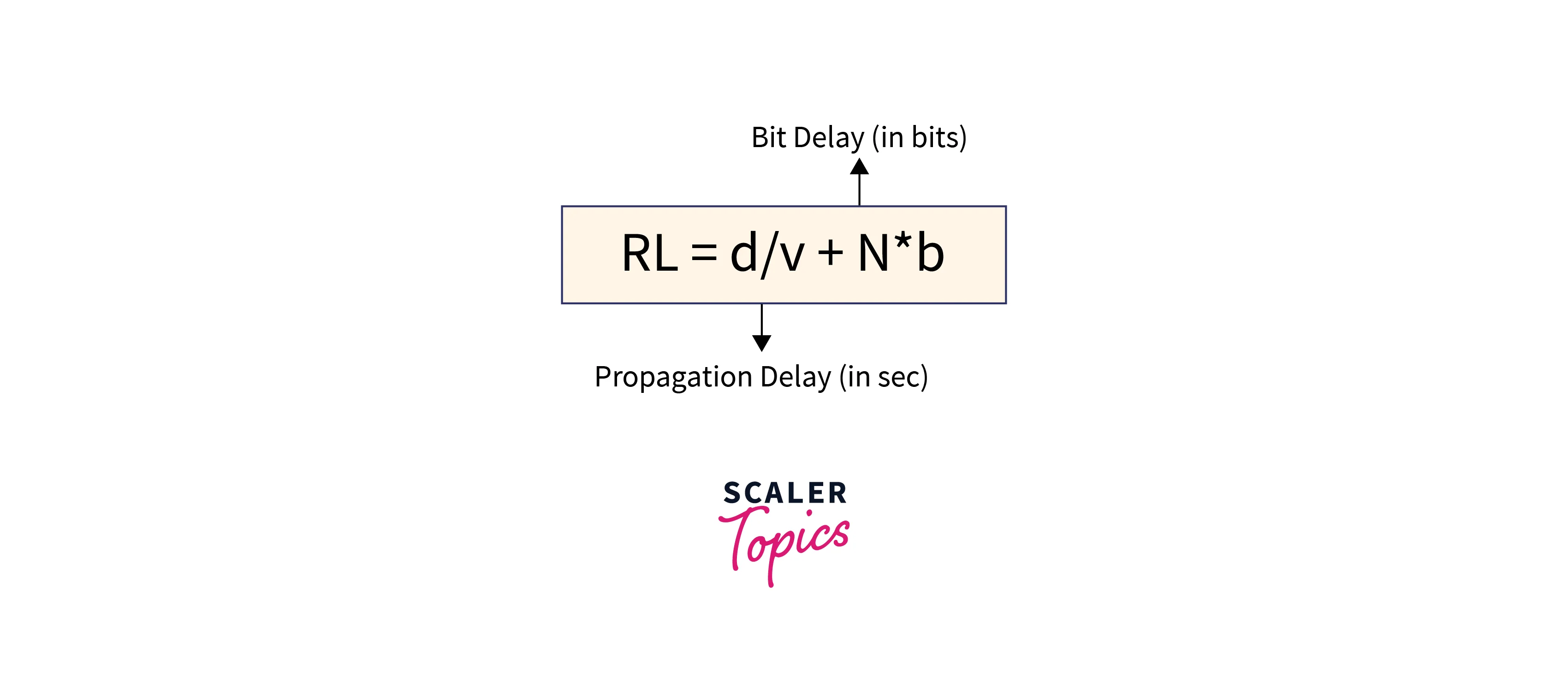
here,
d = ring length
v = data velocity in ring
N = total number of stations in a ring
b = bit delay
Bit delay is the time for which the station holds the bit before its transmission.
is converted into a second then:
–
is converted into bits then:
–
Cycle Time
Cycle time is the time to complete one ring revolution.
p
here, = Token Holding Time
p = Propagation delay ()
Token Holding Time (THT)
Token Holding Time is abbreviated as which represents the maximum time the station can hold the packet. The default value of is 10 msec.
Refer to the below image for the token passing types
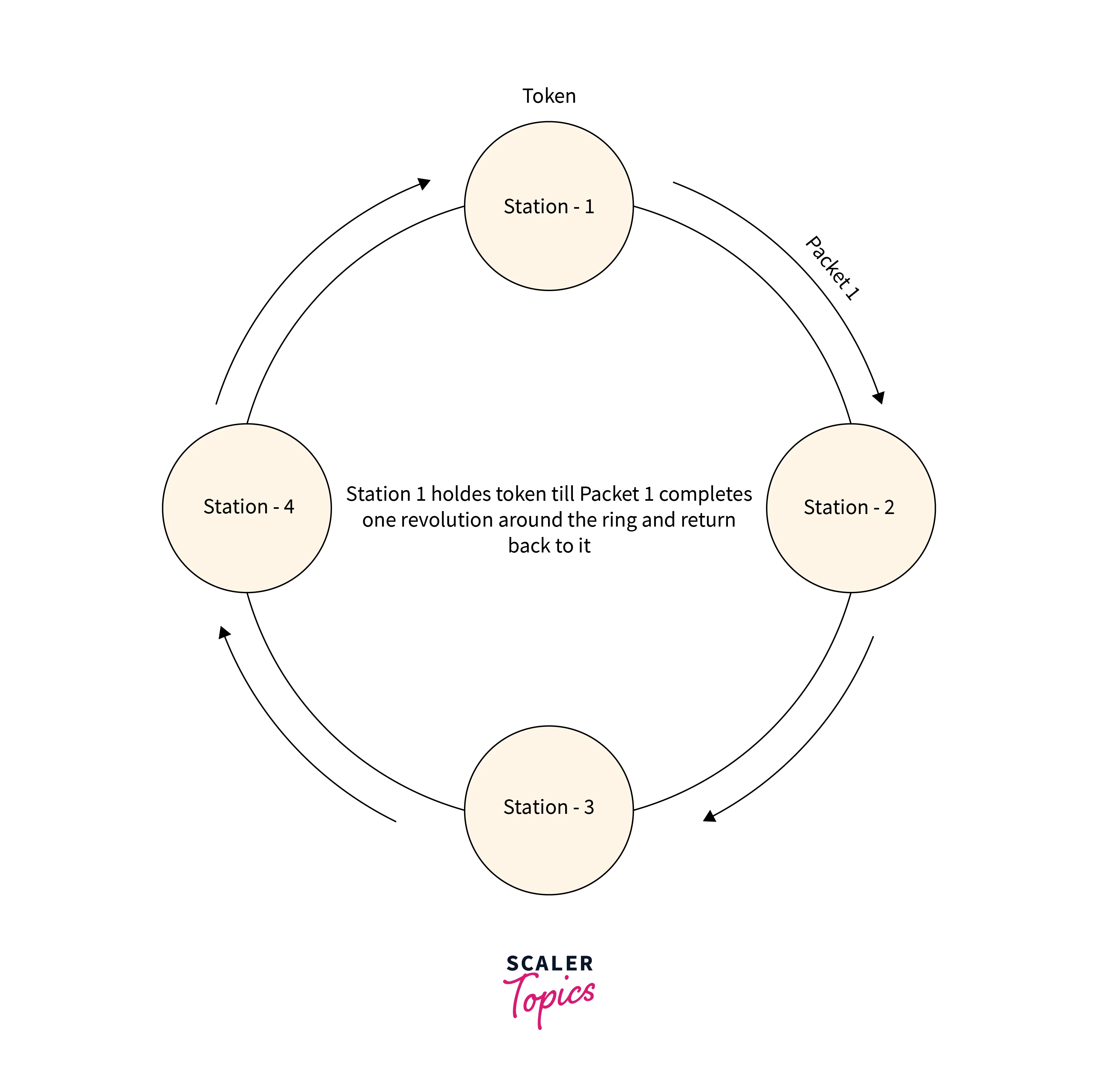
Delayed Token Reinsertion (DTR)
In this after data packet transmission, the station will wait until the packet completes the round trip and return to it. The token is released by the station when the whole packet is received by the receiver.
Refer to the below image for the Delayed token reinsertion (DTR)
t
tp
(Mostly, bit delay=0)
So, tp
here t = transmission delay
p = propagation delay
Efficiency
Efficiency ,
Useful time = t
Total time = cycle time = p
Efficiency, tp
Put the values of and P
t p tp
where pt
here t = transmission delay
p = propagation delay
Early Token Reinsertion (ETR)
The token is released by the station after the data transmission it will not wait for the packet to complete the revolution.
Refer to the below image for the Early token reinsertion (ETR)
t
here, Tt = transmission delay
Efficiency
Efficiency, e = useful time/ total time
Useful time = t
Total time = cycle time = p
Efficiency, tp
Put the values of THT and TP
t p t
where pt ,
t = transmission delay,
p = propagation delay
Physical Layer Of Token Ring
Twisted-pair cable pair covered with the shield is recommended by IEEE 802.5 for the token ring. And this media has a 1 Mbps or 4 Mbps signal speed, but a token ring with a speed of 16 Mbps was released by IBM. 4 Mbps is supported by the adapter of the token ring released by IBM. Digital data encoding is done by the differential 'manchester'. The ring disappears instantly on the failure of the single point. Wire centers are special devices for bypassing the cable's bad segment or the problematic stations of the cable.
IEEE 802.5 Token Ring Frame Format
Refer to the below image for the IEEE 802.5 Token Ring Frame Format
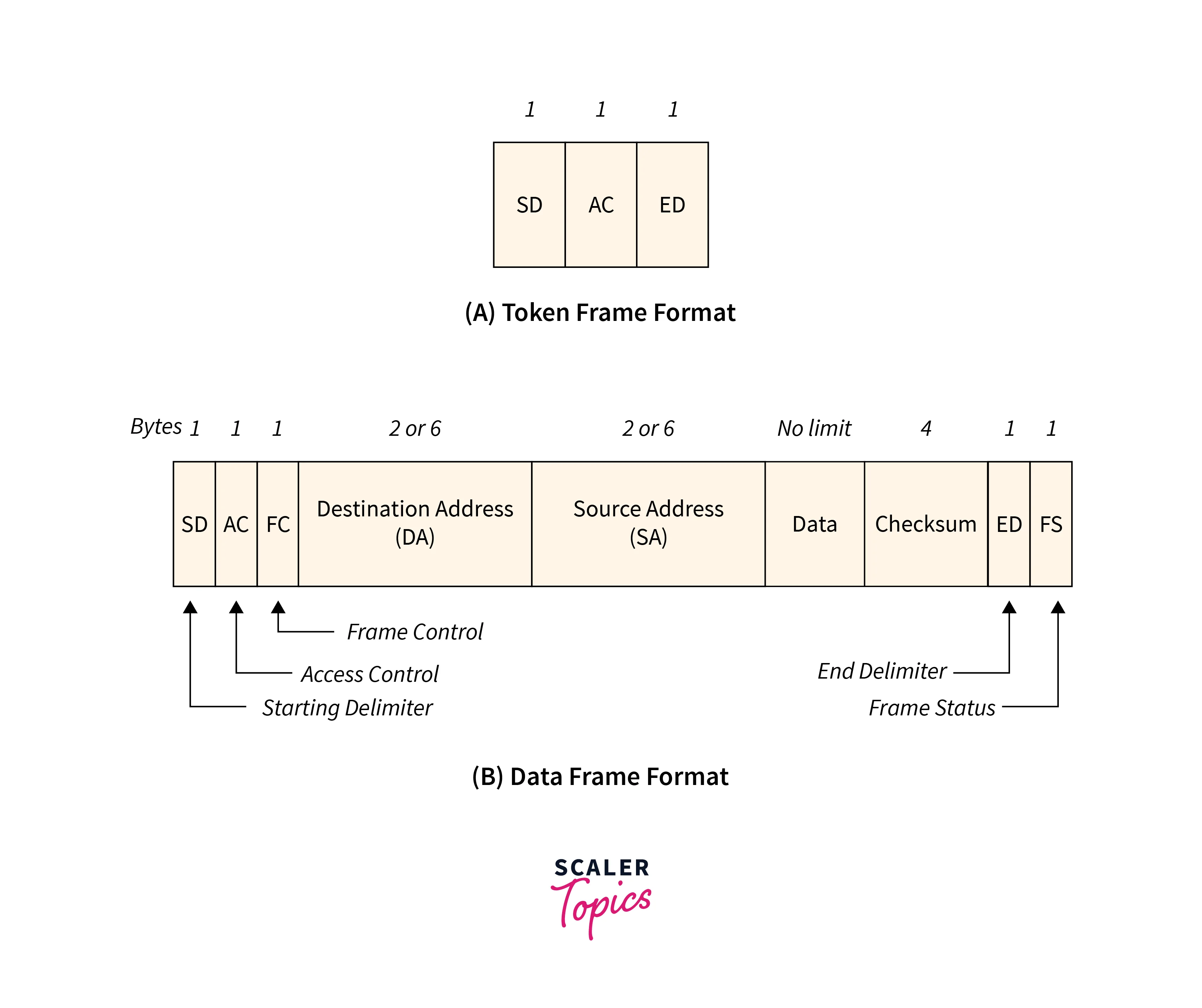
Starting and ending delimiter: Ending and starting of the frame are marked by the starting and ending delimiter. This does not contain the coded patterns of the differential manchester so that it can be easily differentiated from the data.
Access control: 3-byte token with frame's starting and ending is represented by the access control field. While data transmission, reservation, monitoring, and priority are performed in this field.
Frame control: Data field is differentiated from other fields with the help of this field.
Source address and destination address: This field is used to represent the address of the source and destination.
Checksum: The Checksum is used for error detection purposes.
Token Ring Maintenance
There may be a possibility of network fault in the token ring network. So token ring protocol sets one station as an active monitor. Serving as a centralized source of timing-specific data for all the other connected stations in a ring is the main work of an active monitor. It is also used for the maintenance of the network. Maintenance of the ring involves the elimination of frames that endlessly circulate in the ring. There may be some data in the network that continuously circulates in the ring as its sending host fails due to some reason. Due to this other stations in the network were unable to transfer their packet. So it is the responsibility of the active monitor to destroy that data from the ring and generate a new token for resolving this issue.
Possible Errors with Token Ring
In any network, there may be the possibility of some issues but sometimes these may lead to the breakdown of the network. All the computers in the token ring by default work as a standby monitor (SM) and generally network is checked in an active monitor (AM) role. Each station present in the network can play the role of SM. But there is a fixed procedure named token claiming that decides which station acts as AM and which remaining station acts as SM. When the current AM is not transferring the necessary frame through the ring, then token claiming is initiated. The next station present in the ring compares its MAC address with the sender one. If the address value of this station is found to be higher than it, replace the frame with its own. Only one station is left at the end. A new active monitor is determined only If the last station's frame already circles the ring 3 times without the intervention of another station present in the network.
The responsibility for the successful running of the ring is on the active monitor but there are some cases where SM can also intervene in the network. Following are some situations in which the token ring network can heal itself.
Token Gets Lost
When the token passes through the activity monitor it sets a timer. If the timer is over then this token again reaches its origin. AM finds the error in the network and passes a newly generated token.
Package Cannot Find a Recipient
When a packet is transferred by one station and all other stations are unable to work as a recipient for that packet then that packet would circulate endlessly on the ring. At first, when the packet passes the AM, AM is required to convert a specific bit. After this, if the packet again passes through AM, then AM automatically finds out that this particular packet was unable to get to its recipient station. Now only AM can set the bit to 1 and find that it has already come in contact with that particular packet. And now AM eliminates that packet and will generate a new free token.
Faulty Interfaces
Normally in a ring topology, if there is any fault in any connection or station it simply means the entire failure of the network but in a ring topology, if there is any fault in any connection or station it does not lead to the whole network failure. Direct neighbors find out about the faulty stations in the token ring network. To find the default station, a participant sits exactly behind the faulty station and transmits the test frame to the adjacent station. At this time, all other stations go into waiting mode. No station is allowed to transfer any message at this time. Damaged stations find that the neighbor station submits a complaint request, then it begins an error analysis and is removed from the network. There is also a possibility that an error can also occur at the original station. So in this situation, the participants set a timer that allows a neighbor to perform a self-test. If there is no arrival of the frame after the timer expires then it is supposed that the error occurred and a test begins.
How Does Token Ring Compare to Ethernet?
- In the ethernet network, all devices are not allowed to have the same MAC address but in the token ring, all devices can have the same MAC address without facing any problems.
- Cabling in the token ring is more costly as compared to ethernet CAT 3/5e cable.
- Network ports and cards are also costly in token rings.
- A token ring is used when there is a need to prioritize one station over another. As this cannot be possible in Ethernet.
- Tokens are used in the token ring network to eliminate collisions. There are more chances of collision in Ethernet when hubs are used in the network, so they use switches to overcome the problem of collision.
- Ethernet is not suitable for real-time applications due to collision issues.
Conclusion
- Token ring is defined as a communication protocol in a local area network in which all the stations present in the network are connected through a ring topology.
- Token is a small size frame of 3 bytes.
- For the avoidance of network congestion, token rings allow only one device to be active at a time.
- Listen Mode, Transmit Mode, and by-pass mode are the three modes of operation of the token ring.
- Token's main work is to circulate in the network and pass through the stations in the network and allow them to transfer the packet.
- Twisted-pair cable pair covered with the shield is recommended by IEEE 802.5 for the token ring.
- Starting and ending delimiter, access control, frame control, source address and destination address, and checksum are the fields of the IEEE 802.5 token ring format.
- Token ring protocol sets one station as an active monitor for the maintenance of the network.
- There are several problems associated with token rings, such as token loss, package failure, and interface issues.
- For the avoidance of collisions in the network, token rings allow only one device to be active at a time.
