The Ultimate Guide About Wide Area Network (WAN) + MPLS Conf & PPOE Explanation
FORE MORE ARTICLE LIKE THIS, VISIT MY WEBSITE:
https://www.techguruhub.net/2022/01/30/wide-area-network-ultimate-guide/
Wide area network
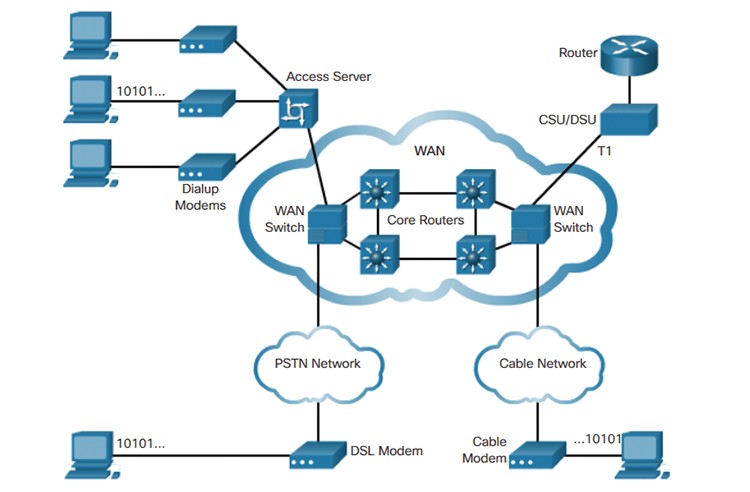
The phrase wide area network is used to describe a network that covers many geographic regions. Consider an example. A firm has two offices, one in London and one in Berlin. Both offices have a LAN. If the corporation joins these two LANs together via WAN technology, a WAN is established.
The fundamental distinction between LANs and WANs is that the corporation normally doesn’t own WAN infrastructure. A corporation commonly leases WAN services from a service provider. A WAN spanning numerous towns may look something like this:
Wide Area Network Example Graphic.
Frame Relay, ATM and X.25 are several kinds of WAN technology. The Internet may also be called a WAN.
Cisco VPN - What is VPN (Virtual Private Network)?
Security is vital in today’s society because of new risks begun by hackers willing to attack your network and resources. There are three states of data that we need to secure — data at rest, data in use, and data in transit. Data in transit is more susceptible to assaults since the data will move beyond your secured network. The safest and cheapest approach to safeguard our data in transit is by utilizing Virtual Private Network (VPN) . Cisco VPN solutions are available as well.
Why Do We Need VPN?
A Virtual Private Network (VPN) is an encrypted tunnel between two or more devices, generally a firewall, such as the Cisco Adaptive Security Appliance (Cisco ASA), across an unprotected network such as the internet. All the network traffic that is routed over the VPN tunnel will be encrypted and kept secret from hackers on a network or the internet. VPN substitutes the dedicated point-to-point link with the simulated point-to-point link or secure connection that shares the common infrastructure.
Using VPN will cost you nothing since it is entirely free as most firms have firewalls already installed with a built-in VPN function. VPN also offers protection for all the traffic that is transmitted outside your network using VPN tunnels. Lastly, VPN is expandable in that you can add infinite tunnels and users.
Two Types of VPN
There are two sorts of VPN that we are routinely employing, and both are secured but installed and utilized in various ways.
- Site-to-Site VPN
Organizations are continually growing into other branches, and to safeguard the data in transit between two branches, we need to build a site-to-site VPN. Common VPN protocols used in site-to-site VPN include Internet Security Protocol (IPSec) (IPSec). In deploying this form of VPN, we need to set up the Phase 1 and Phase 2 VPN agreements. IKE Phase 1 negotiation is when we construct a safe encrypted channel or encrypted network communication so the two firewalls may start the Phase 2 discussion.
In IKE Phase 2 negotiation, the two firewalls will agree on the set parameters that specify what traffic may travel across the VPN tunnel and how to authenticate and encrypt the data. The arrangement is named Security Association. Both Phase 1 and Phase 2 should contain the same settings, such as pre-shared keys, authentication, encryption, and IKE version.
There are two approaches to establish site-to-site VPN:
Intranet VPN — it offers protected site-to-site access inside the firm or internally.
Extranet VPN — it offers encrypted site-to-site communication outside the enterprise. For example, clients or partners may securely access the pooled resources of the organization.
The accompanying graphic depicts the Site-to-Site VPN implementation:
Cisco VPN Remote Access VPN in details.
2. Remote Access VPN
Commonly termed a mobile VPN. Using this form of VPN connection lets the users to connect over the internet anywhere in the globe to access the business network resources safely. It may be utilized in a work-from-home scenario where the workers can safely access the company’s internal resources using a VPN. On do this, the employee must install a VPN client, such as a Cisco anyconnect secure mobility client or Cisco anyconnect VPN client, to their device, and a virtual IP address will be issued to the employee’s device/PC that will be used to build a protected tunnel.
Remote access VPN may employ SSL, IKEv2, L2TP, and IPSec protocols. The most secure and easiest to deploy protocol is IKEv2. Some internet connections prohibited the IKEv2 and L2TP protocols. That is why some are adopting SSL VPN since it utilizes the usual HTTP/HTTPS communication that is permitted on all internet connection types. IPSec for remote access VPN is not commonly utilized, since there is already a known weakness on the protocol.
The system administrator may select between two options to install the remote access VPN:
Full Tunnel - all the traffic that is flowing out from the employee’s device will go straight to the firewall, and the firewall will pass it to the internet if required. This is a totally protected solution since all the security services of the firewall will be applied to all the traffic flowing out from the employee’s device.
Split Tunnel - the traffic that will go to the internet like HTTP/HTTPS traffic will travel to the standard internet connection such as broadband/LTE, while the VPN traffic will be used to access the internal resource of the organization will use a VPN tunnel. The traffic will be separated depending on its purpose.
The next graphic depicts the Remote Access VPN implementation:
WAN Connection Types – Explanation and Examples
Organizations are continually growing into numerous sections with different locations. To link the two branches, we are utilizing the infrastructure of Internet Service Provider to offer connection between the branches. The network link outside of the organization’s network is termed Wide Area Network (WAN) (WAN).
The ISP is giving us with a subscription-based WAN connection type allowing us to have access to our resources remotely. Another significant use of WAN is the internet. We can connect to the internet because of the WAN supplied by our local Internet Service Providers. We’ll explore each WAN connection type below.
Wide Area Network Connectivity
Wide Area Network (WAN) is a telecommunication network that is used to simply expand a LAN across a big geographical region. Technically, two or more local area networks may be linked through WAN using separate layer 3 devices like routers or firewalls.
Most WAN IP address utilizes the static public IP address, dynamic public IP address, and PPPoE (Point-to-Point Protocol) as the connection to the ISP depending on the subscription. Static public IP addresses are significantly costlier as opposed to dynamic and PPPoE since we only have limited unique public IP address that cannot be reused by other customers. Private IP addresses are only routable on the local network and not routable across WAN or the internet. The following diagram depicts the LAN and WAN infrastructure.
READ: Cisco IOS Ultimate Guide
WAN Connection Types
There are several WAN connections that we employ to offer our access to the internet. Below are the typical alternatives for WAN connection from the internet provider.
Leased Line
This WAN connection type is a dedicated point-to-point link and fixed-bandwidth data connection. By employing leased lines, your network will have a totally protected and stable connection, high bandwidth, and improved quality of service. On the other hand, leased lines might be costly and not expandable since it is a permanent physical connection.
Digital Subscriber Line
DSL is a medium used to carry digital signals over the regular telephone lines. It utilizes a separate frequency than the telephone is utilizing so that you may access the internet while making a call. DSL is an older idea that gives an average speed of roughly 6mbps. The positive part with DSL is the bandwidth is not shared and delivers a steady speed.
Cable Internet
One technique to establish broadband internet access is by utilizing cable internet from a local cable TV provider. It has quite a resemblance with DSL since it also leverages an existing cable modem from cable TV to deliver data. On this connection, the speed fluctuates with the number of users on the service at a certain moment.
Fiber Internet Access
It is the newest broadband connection that gives the best internet speed service to the clients. It is also often used in telecommunication backhaul connections because of the greater speed it can carry as compared to other cables. DWDM, SONET, and SDH are the ISP backhaul transfer equipment that employs fiber optic cable. Fiber optic is also utilized in telecom packet switching networks or circuit switching networks.
Multi-Protocol Label Switching (MPLS)
MPLS is a sort of VPN that utilizes labels on forwarding packets instead of IP addresses or layer 3 headers. It delivers maximum security and routing for customer’s locations. On MPLS, the service provider is participating in the customer’s routing.
Wireless WAN
Most of us are using mobile phones that utilize mobile data to connect to the internet. The frequently recognized connection types for wireless WAN include 3G, 4G, LTE, and 5G. It is the services supplied by local ISP to allow wireless internet access to mobile devices using cellular sites. It employs certain frequencies to deliver larger coverage and better signal to clients.
Leased Line Definition, Explanation, and Example
Local Area Network (LAN) is where we link the endpoint devices like servers, workstations, telephones, and access points. To link the device inside the LAN to a different device within the separate LAN, we are employing a Wide Area Network (WAN) (WAN). In WAN, two or more local area networks might relate to distinct layer 3 devices like routers or firewalls. The usual kind of WAN is leased line connection.
Understanding Leased Lines
A leased line, commonly termed a dedicated line, is a dedicated point-to-point link and fixed-bandwidth data connection. A leased line is not a dedicated cable. It is a reserved dedicated leased line circuit (either a copper or a fiber optic cable) connecting two sites.
The leased line sends data in both directions utilizing a full-duplex transmission. It employs two pairs of wires (full-duplex cable), that each wire is employed in a unidirectional transmission of data network. A leased line is not a lengthy physical connection stretched to two or more places as some imagined. It employs a specialized switching device that functions as a signal amplifier to make the connection a point-to-point link and reach a distant destination.
Organizations are not constructing their infrastructure to make a dedicated link to their other branches since it is costly and complex to install. They utilize the infrastructure of an Internet Service Provider on a set monthly charge, which is why it is termed a leased line.
The accompanying figure depicts how the leased line links two branches:
ISP as a Leased Line
A leased line may be of any media as long as it links two branches together regardless whether it has network circuits in between. It might be an MPLS, Fiber Optic, DSL, or Satellite. The local Internet Service Provider is the ideal approach to get a leased line since they have a big geographical network infrastructure. It may either be a monthly or annual subscription, depending on the agreements with the ISP.
From the Optical Network Terminal (ONT) positioned on the customer’s branch, the traffic will move to the Optical Line Termination (OLT) located in the ISP premise, where it multiplexed and processed all the optical signals originating from the customers.
From OLT, it will then proceed to the edge routers where it utilizes VRF and adds labels if it is using MPLS. From edge routers, it will then move to the core router using BGP as the overlay protocol and IGP like OSPF as the underlay protocol. From core routers, it will send the data to the other edge router, proceed to OLT, and lastly to the ONT, which is situated to the other branch of the client. The transmission equipment utilized in between the core routers, edge routers, OLT, and ONT is either Synchronous Digital Hierarchy (SDH) or Dense Wavelength Division Multiplexing (DWDM) (DWDM).
Lease Line Advantages and Disadvantages
Most leased lines have a Service Level of Agreement (SLA) to the ISP, which assures a dependable and steady internet connection. Because the leased line is a dedicated communication channel, your network will have stable internet connectivity, continuous data flow, increased bandwidth may be attained and regulated. You may install a leased line when you want a totally protected and improved quality of service for your network.
On the other hand, leased lines may be costly since they require a dedicated cable and switching equipment. Not only that, the leased line is not expandable since it is a permanent physical connection.
READ: Cisco IOS Ultimate Guide
Multiprotocol Label Switching (MPLS) Overview
The classic router-based network connects each peer site by dedicated point-to-point connections or leased lines. That solution is costly, not scalable, and needs lengthy and difficult implementation, while it guarantees a totally secure and dependable connection, high bandwidth, and quality of service. Another method that emulates the point-to-point connections is by employing Multi-Protocol Label Switching (MPLS) services with the same and higher quality of service.
Virtual Private Network (VPN) Models
VPN may be constructed based on two models:
• Overlay Model
The local ISP offers a virtual point-to-point connectivity between subscribers. Commonly used overlay VPNs include IPSec, GRE, and frame relay.
• Peer-to-peer Model
The local ISP participates in the customer route. A typical example of a peer-to-peer model is MPLS.
What is Multi-Protocol Label Switching (MPLS)?
MPLS is a technique of forwarding IP packets by utilizing labels instead of IP addresses or layer 3 packet headers. It combines the best aspects of the Overlay and Peer-to-peer approach. Because it employs labels, it speeds up packet forwarding and IP routing. It eliminates the processing burden of IP inspection while performing a typical routing procedure.
MPLS Operation
On a regular routing procedure, the router receives the packet, verifies the layer 3 header, and retrieves the destination IP address to decide which way the packet should follow. The router always examines the routing table while sending the message. On an MPLS network, the router just checks on the label, which lowers the overhead processing and enhances the speed of the network.
The accompanying figure explains how labels are exchanged on each router.
NOTE Label Switched Pathways (LSPs) are preset and unidirectional paths between the MPLS routers. When a packet reaches the network via a Label Edge Router, also known as a “ingress node”, it is given to a Forwarding Equivalence Class (FEC), based on the kind of data and its intended IP addresses, either IPv4 or IPv6, to identify endpoints and intermediary switches and routers.
The accompanying diagram displays the MPLS networks. The customer edge router (CE) route traffic to Provider Edge (PE) routers, and each router has its own segregated routing table instance on the PE router. The core routers do not contain customer route information. The label switching is enabled in ISP core routers.
mpls network
NOTE Penultimate Hop Popping (PHP) reduces the necessity for the double lookup to be done on an egress router (PE) (PE). It enhances the MPLS performance.
MPLS LDP Configuration
MPLS does not forward the label automatically. It employs Label Distribution Protocol (LDP) to distribute labels on every router inside the ISP core network. We will use the following network diagram for our setup example.
- Configure the IP address on each interface and the IP address for loopback 0. Configure the inner gateway protocol (IGP) on each router and advertise each route on the network.
Router1:
co
conf t int g0/0 ip address 10.1.1.1 255.255.255.0 no shut ip ospf 1 area 0 int lo0 ip address 1.1.1.1 255.255.255.0 no shut
Router2:
conf t \sint g0/1 \sip address 10
conf t int g0/1 ip address 10.1.1.2 255.255.255.0 no shut ip ospf 1 area 0 int g0/0 ip address 20.1.1.2 255.255.255.0 no shut ip ospf 1 area 0 int lo0 ip address 2.2.2.2 255.255.255.0 no shut
Router3:
conf t int g0/1 ip address 20.1.1.1 255.255.255.0 no shut ip ospf 1 area 0 int g0/0 ip address 30.1.1.1 255.255.255.0 no shut ip ospf 1 area 0 int lo0 ip address 3.3.3.3 255.255.255.0 no shut
Router4:
conf t int g0/0 ip address 30.1.1.2 255.255.255.0 no shut ip ospf 1 area 0 int lo0 ip address 4.4.4.4 255.255.255.0 no shut
- Check whether Cisco Express Forwarding is activated on each router.
Router#show ip cef
- Configure LDP on each router.
Router(config)#mpls label protocol ldp Router(config)#mpls ldp router-id loopback 0
- Activate MPLS in each router’s interface.
Router(config)#interface Router(config-if)#mpls ip Router(config-if)#end
- The following show command will be used to check that packets are routed based on label search.
Router#show mpls neighbor Router#show mpls interfaces Router#show mpls ldp bindings
READ: Cisco IOS Ultimate Guide
What is PPPoE? Point to Point Protocol over Ethernet
Point-to-Point Protocol over Ethernet (PPPoE) is a protocol in networking that is frequently used by Internet Service Providers (ISPs) to deliver digital subscriber line (DSL) high-speed Internet services. Point-to-Point Protocol over Ethernet employs conventional techniques of encryption, authentication, and compression provided by PPP and is defined in RFC 2516.
Obtaining IP Addresses
We don’t have to set IP addresses manually since the ISP dynamically allocates IP addresses from its address pool to customers who are permitted to get one. Whilst a PPPoE session is started, the IP address is only utilized when the session is active. The IP address is relinquished when the connection is finished, allowing for efficient re-use of IP addresses.
PPPoE Explained
Point to Point Protocol over Ethernet Features
Below are the characteristics of Point Protocol over Ethernet (PPPoE):
- Multi-Link PPPoE (MLPPP) — a unique WAN option that combines several PPPoE lines from the same ISP to make one bigger virtual circuit.
- RADIUS Server - PPPoE server may utilize it to conduct authentication, authorization, and accounting for access users.
- MPLS network may be set up through PPPoE interfaces.
- Data Compression - by compressing the data, the information communicated from one user to another would become smaller, which implies that the transmission of data will become quicker and more efficient.
- Encryption - encrypting the data helps safeguard the user and the networks from dangerous applications and users.
- Quality of Service (QoS) - a way to manage traffic and assure the performance of key applications, and there are specific QoS settings available for the PPPoE protocol.
- Authentication Protocols:
- Password Authentication Protocol or PAP — communicates in cleartext. There’s no encryption of the information that you’re transmitting.
- Challenge Handshake Authentication Protocol or CHAP – was established to give extra security to this authentication procedure. It employs encrypted challenge to be able to communicate the credentials over the network.
PPPoE Operation
Listed below is the sequence of how PPPOE works:
PPPoE Active Discovery Initiation (PADI) — Client delivers PADI frame through layer 2 broadcast.
PPPoE Active Discovery Offer (PADO) - Server answers with its MAC Address, name, and the name of the service.
PPPoE Active Discovery Request (PADR) - Client verifies acceptance of the offer of a PPPoE connection provided by the server.
PPPoE Active Discovery Session-confirmation (PADS) – Server verifies PADR and answers with PADS including a session ID. The connection has now been completely established.
PPPoE Active Discovery Termination (PADT) — This Ethernet transmission ends the PPPoE connection and may be triggered from either the client or the server side.
PPPoE versus DHCP
Dynamic Host Configuration Mechanism (DHCP) is a protocol for getting IP addresses from DHCP servers, whereas Point-to-Point Protocol over Ethernet is a way of connecting to an ISP.
DHCP setting is quite popular and is frequently utilized, but PPPoE is steadily slipping out of favor.
You would need to have the right credential (username and password) with PPPoE, whereas the setup on the DHCP client is automated.
The Different Wide Area Network (WAN) Topologies
Wide Area Network (WAN) handles the diverse geographical locations, such as branches on any other site or distant location, issues that a LAN normally experiences. We are going to tackle the diverse network topologies that meet the varied scenario required by customers whereby the service provider delivers their WAN services to link their clients’ sites for a particular amount depending on the need such as capacity, availability, and speed.
We will be covering the prevalent WAN technology nowadays, such as Metro Ethernet (MetroE), whereby it employs physical Ethernet lines to connect the customer’s network devices to the service provider’s network and other WAN topologies that are utilized today. To be able to link numerous locations via Wide Area Network, the service provider should be fully informed of the topology to be employed to satisfy the business client’s demands.
Point-to-Point
The client just desires simple point-to-point network connection between two facilities separated geographically that will enable them to transmit and receive Ethernet frames to each other as if they are linked directly. Point-to-point architecture is invisible to the consumer network and works as if there are physical connections between distant facilities.
Typical dedicated leased lines connections are supplied with this form of arrangement, such as an E1 or T1 line. But with MetroE, service providers provide what is termed an Ethernet Line Service or E-Line where two customer premise equipment (CPE) devices may exchange Ethernet frames, similar in concept to a leased line.
Point-to-Multipoint
This WAN architecture needs a central site device that directly delivers Layer 2 frames to reach distant sites, while the remote sites can only send frames to the central site. This Metro Ethernet service is known as E-Tree, whereby the central site is the E-Tree Root and the peripheral sites are the E-Tree leaves. This topology is also known as Hub and Spoke or partial mesh network topologies, but regardless, this form of WAN topology offers a service that satisfies the requirement to have a hub site with numerous sites linked.
Full Mesh
Full mesh topology allows all the connected devices in the WAN topology to communicate with each other, and the people who develop MetroE has anticipated that there is a need for full-mesh connectivity of devices wherein they all send and receive Ethernet frames to each other directly without having to be dependent on a central hub. This MetroE service is termed Ethernet LAN or E-LAN.
An E-LAN service lets all the devices connected to it to transmit frames directly to one other as if they are in one huge Ethernet switch.
Ring Topology
This topology is nearly like a point-to-point but is linked on both sides to give protection just in case a problem arises. WANs that employ this topology are less prone to failure as traffic may be routed the opposite way around the ring if a defect is discovered on the network. But, adding additional sites to the ring topology needs more labor and money compared to a simple point-to-point configuration since each new site will require double the connection required.
Star Architecture \sWAN topology employing the star network design needs a central hub. A concentrator router is being utilized to verify that data is appropriately transmitted to the destination. This architecture offers simpler integration of additional network components to the network, which may be an essential aspect for commercial WANs since it requires less time and expense.
This design also makes the network less susceptible to a single point of failure problem that may disrupt traffic on the network except for the central hub. The spokes have an independent connection in transferring data to the concentrator router, which means they do not rely on other spokes to work well and can simply pinpoint the problem if ever anything wrong occurs.
Star Topology
A central hub is required for WAN topology utilizing the star network setup. To guarantee that data is correctly transported to the destination, a concentrator router is employed. This design facilitates the addition of new network components to the network, which may be a significant benefit for commercial WANs because it saves time and money.
This architecture also reduces the risk of a single point of failure, which might disrupt traffic on the network except for the central hub. The spokes have their own data transmission link to the concentrator router, which means they don't rely on other spokes to work well and can quickly pinpoint the problem if something goes wrong.